What is Trojan Powelik Activity?
Just as its name implies, Trojan Powelik Activity is a Trojan horse used to invade user’s computer. The publisher of Trojan Powelik Activity utilizes it to steal personal information such as credit card information, or attack user’s computer maliciously causing breakdown of system. To summarize, Trojan Powelik Activity is a severe security threat.
Trojan Powelik Activity is a new virus and it has some symptoms when your computer is infected. Initially, massive processes slow down and freeze. Even you are not on the internet, there are strange music and TV shows coming across the screen with no visible ads or popup displayed. Sometimes, the baleful virus occupies high RAM so that computer experiences occasional BSOD. Yesterday, an affected friend told me he ran Norton Power Eraser by fast scan mode, but it had no effectiveness helping the issue.
On the other hand, when Trojan Powelik Activity slips into the machine, it will hold a backdoor for cybercriminals. So criminals can readily use the leak to lead uses to wrong websites aiming to get pay-per-click revenue.
How does Trojan Powelik Activity distribute into our PC?
Trojan Powelik Activity specializes at some harmless files bundled with freebies. As soon as you down load these documents from some third-party platform or suspected websites, the virus will perform acting load automatically. After finishing, it begins to execute and create the following registry entries:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\"(default)" = "[ENCRYPTED JAVASCRIPT]" HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\"[NON-ASCII STRING]" = "rundll32.exe javascript:\"\..\mshtml,RunHTMLApplication \";document.write(\"\74script language=jscript.encode\"+(new%20ActiveXObject(\"WScript.Shell\")).RegRead(\"HKCU\\software\\microsoft\\windows\\currentversion\\run\\\")+\"\74/script\")"
Next, Trojan checks whether the compromised computer installed Powershell or NET framework. If not, it will down load the installers from the official Microsoft website.
The following step is that your computer may be puppet by remote attack when Trojan connects to the locations (178.89.159.34, 178.89.159.35) through Powershell or NET framework.
How to remove Trojan Powelik Activity manually?
When your PC is infected, you can remove the virus by yourself. It is noteworthy that you should delete infected files and registry entries, otherwise, the virus will recover or you may damage your computer by some mistakes. The process requires you have enough computer knowledge and skills.
Step 1: restart your computer in safe mode.
For Windows 7/Vista/Xp, press F8 repeatedly before the Windows 7/Vista/Xp splash screen appears. When Advanced Boot Options screen shows up, select safe mode and press ‘Enter’ to proceed.
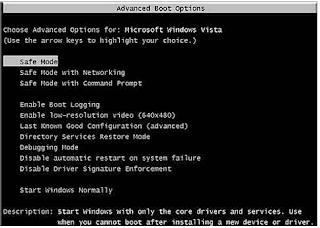
Step 2: delete files created by Trojan Powelik Activity.
Firstly, you should change the Folder Options settings to find hidden and protected files because the Trojan may create its files in hidden folders. Now you could click ‘start’ button, go to Control Panel and then access into Appearance and Personalization and click Folder Options.
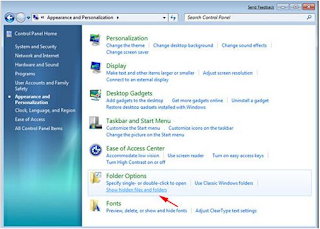
Next, under Advanced settings contained in View box, click Show hidden files, folders, and drives, and then press OK.
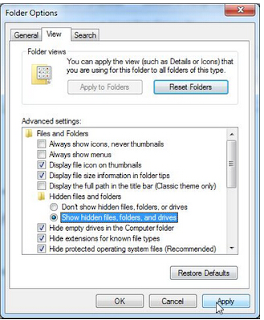
Step 3: delete the registry entries created by Trojan.
Input ‘regedit’ in search box, and press Enter.
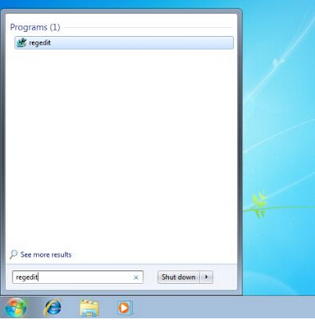
Next, click on Yes when you are prompted by UAC.
When Windows registry editor opens, search for the infected registry entries and delete them.
Sterp 4: restart your computer in normal mode.
How to remove Trojan Powelik Activity with SpyHunter?
Operating manually, I have to say honestly, exists risk of damaging computer or getting rid of virus incompletely. In my opinion, using a reputable and reliable antivirus is optimal and convenient choice.
SpyHunter is a famous antivirus around the world. Now I help you how to use it.
Step 1: Please click this download icon below to install SpyHunter.
Step 2: Now, I will help you install SpyHunter step by step.
After you finish downloading, perform the file and click ‘Run’ icon.
Then accept the license agreement and click on ‘Next’.
Next, the setup process will perform automatically until it finishes.
Finally, you should start the antivirus and scan your computer completely.
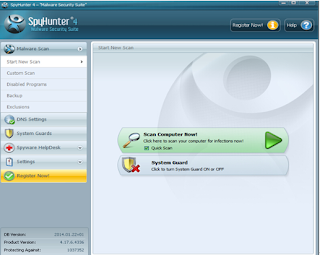
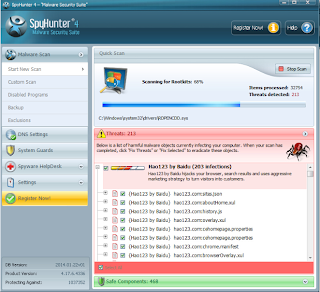
If you find threats below, delete them.
In addition to use SpyHunter, you could select Recgure Pro, which is an advanced registry clear pro. Recgure Pro can optimize your RAM and clear useless registry entries in order to ensure your computer in a safe situation.
Step 1: click the hyperlink below to down load Recgure Pro.
Step 2: install the Recgure Pro.
After you finish down loading, click ‘Run’ button, press ‘Next’ button and accept agreement. Next, the installation will perform automatically.
When you accomplish installation, run scan with the software and delete the threats listed.



No comments:
Post a Comment