What is CryptoWall 3.0?
CryptoWall 3.0 is an advanced version of CryptoWall 2.0. Compared with CryptoWall 2.0, it has more complicated encrypting system and difficult to eliminate. CryptoWall 3.0 is a notorious ransom aiming to deceive customers’ money through encrypting the files. Unlike adware, this type of ransom malware poses a huge threat to our life. It makes locked files useless. What it worse, there is no way to recover the files encrypted unless you pay for the cybercriminal. This forcing behavior is illegal and has negative effect on our daily life. As the features of CryptoWall 3.0, personally, precaution is much more significant than finding a way to recover the locked files after removing the virus.
CryptoWall 3.0 targets all versions of Windows system. Compared with the old version, CryptoWall 2.0, the newest has long deadline for victims to pay for the key. When the victims fail to find a solution with spending much time, they have to pay for the decrypting key. It is the strategy set by criminals.
How to prevent CryptoWall 3.0?
CryptoWall 3.0 often infects computer through spam emails or some freebies downloaded from third-party platforms. So I suggest that the computer users should not open suspected email or open downloading files without antivirus scan. In addition to the two ways, CryptoWall 3.0 can hide itself in some advertisements whose hyperlinks connect to malware’s domain. Please be careful about informal ads.
Restore your files by using native Windows features
To restore the files usually is an effective way to prevent the malware. In general, there are two convenient methods to operate. One is by using mobile HDD (hard disk drive). The other is by using native Windows features. At the following steps, I have emphasis on the second method.
Right-click on the file→go into Properties→select the Previous Versions tab. This tab displays all copies of the file that have been stored and the date they were backed up as shown in the image below.
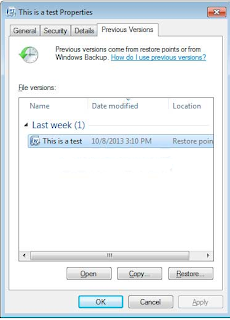
Then select the file you want to restore and the files restore to the previous version.
Remove CryptoWall 3.0 manually
Step 1: reboot your computer into safe mode.
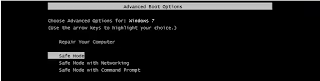
And then, please wait the loading until the system enters into safe mode.
Step 2: click on ‘start’ and input ‘regedit’
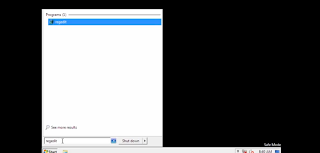
Step 3: find HKEY_MACHINE, enter it and select the two files like the screenshot and delete them.
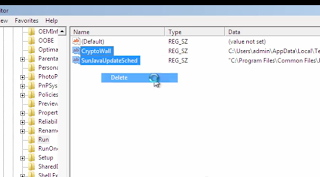
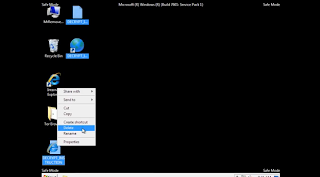
Step 4: return to the desktop, delete the remnants.
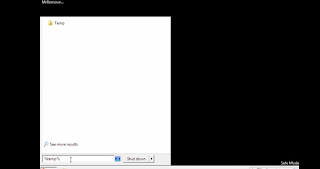
Step 5: input ‘%temp%’ in the search box under the ‘start’ menu.
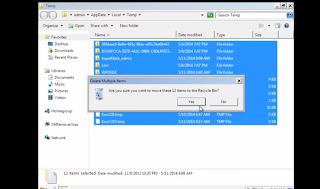
Step 6: select all items in the box and remove them.
Step 7: finally, restart your computer into normal mode.
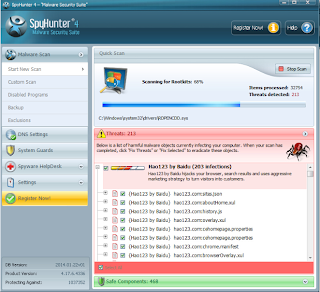
How to remove CryptoWall 3.0 with SpyHunter?
Step 1: Please click this download icon below to install SpyHunter.
Step 2: Now, I will help you install SpyHunter step by step.
After you finish downloading, perform the file and click ‘Run’ icon.
Then accept the license agreement and click on ‘Next’.
Next, the setup process will perform automatically until it finishes.
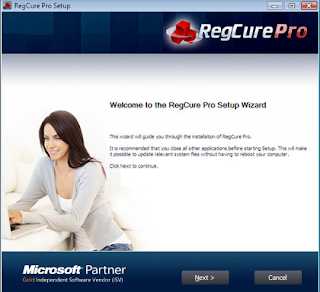
Besides the elimination of infected files and virus, sweep away registries is also significant, which can prevent the virus from recovering. Aiming at this point, you could select Recgure Pro, Recgure Pro can optimize your RAM and clear useless registry entries in order to ensure your computer in a safe situation.
Step 1: click the hyperlink below to down load Recgure Pro.Step 2: install the Recgure Pro.
After you finish down loading, click ‘Run’ button, press ‘Next’ button and accept agreement. Next, the installation will perform automatically.
When you accomplish installation, run scan with the software and delete the threats listed.

Final tips:
I will give you more information about the CryptoWall 3.0 which is helpful to delete the malware manually.
Associated CryptoWall 3.0 Files:
%Temp%\
%MyDocuments%\AllFilesAreLocked
%MyDocuments%\DecryptAllFiles
%MyDocuments%\
%WinDir%\Tasks\
File Location Notes:
%Windir% refers to the Windows installation folder. By default, this is C:\Windows for Windows 95/98/ME/XP/Vista/7/8 or C:\Winnt for Windows NT/2000.
%Temp% refers to the Windows Temp folder. By default, this is C:\Windows\Temp for Windows 95/98/ME, C:\DOCUMENTS AND SETTINGS\
%MyDocuments% refers to the Documents folder for your user profile. By default, this is C:\Documents and Settings\
Associated
HKEY_CURRENT_USER\Control Panel\Desktop "Wallpaper" = "%MyDocuments%\AllFilesAreLocked
If you cannot resolve the problem yet, leave a message to me or download the SpyHunter and Recgure Pro, which can help you as soon as possible.


I have been using AVG protection for a few years, and I'd recommend this solution to everybody.
ReplyDelete